|
|
 |
|
 |
|
 |
| |
Secure your PC with 1st Security Agent. It offers an administrative support for controlling which users are allowed to access your PC and the level of access each user may have. You can restrict access to Control Panel applets, disable Start Menu items, lock local, network and USB drives, disable DOS, boot keys, Registry editing, taskbar, task manager, and network access, hide desktop icons, password-protect Windows and restrict users to running specific applications only. Secure Internet Explorer, disable individual menu items, prevent others from editing Favorites, disable individual tabs in the Internet Options dialog, as well as specific settings from each tab. It also offers a flexible and complete password protection. Excellent online help is available. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
Password protect your computer and restrict access to it with Security Administrator. It enables you to impose a variety of access restrictions to protect your privacy and stop others from tampering with your PC. You can deny access to Control Panel applets, disable boot keys, context menus, DOS windows, Registry editing, Internet and network access. Hide your desktop icons, local, network and USB drives, Start menu items, taskbar, apply password protection to Windows and restrict users to running specific applications only, control Internet usage, view statistics of computer use by your kids or employees. The program also has a built-in lock screen utility to prevent PC entry with a password while you are away. Excellent online help is available. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
This is mass-mailing software used by various e-commerce providers to deliver personalized email messages to customers. The main features are: high speed; unlimited number of customers and customer data fields; support of plain-text, rich text and HTML message formats; message templates and macro definitions for message personalization; Import and Export features for customer database sharing with spreadsheet or database management systems using the standard CSV plain-text file format. User interface is easy-to-use and it is designed strictly according to Apple's guidelines.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
This is a SMTP server program for Windows that lets you convert any Windows based PC into SMTP server. Use it either on a dedicated server or on a personal computer in the background. Any mailer or email program working on the same computer or on a separate computer can connect to the server using TCP/IP protocol. Traveling laptop PC users may use it as a gateway SMTP server that either sends your messages directly when possible or redirects them to other SMTP accounts if direct sending is blocked by the current ISP. The program offers you a lot of security options to protect your machine from hacker attacks and filter SPAM.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
Email and subscription-based mailing lists have become an important feature for many web sites and individual PC users. Mail Bomber is one of the best subscription-based email tools for Internet, it is intended for sending requested personalized email messages to your customers or friends utilizing subscription-based mailing lists. It allows you to create and manage subscription-based mailing lists, and generate individual email messages from predefined templates while sending. You can use it as a handy tool for keeping feedback from your customers or friends, as a manager of your subscription-based mailing lists, or as a simple and handy email program. Online help is available. Try our Internet and email tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
Turns your personal computer into an Internet kiosk or a public access workstation by disabling access to files installed on your PC while giving full access to all necessary applications you specify including Internet Explorer. It supports multiple security modes providing you with an ability to specify the most acceptable type of access to a locked desktop such as username and password authentication, time-locked code (that allows users to access workstation for a given period of time only) or a combination of both. It is ideal for public libraries, Internet cafes, information terminals, in-store kiosks, or home PCs to limit children activities. Excellent online help is available. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
1st Network Admin offers a comprehensive protection for Windows-based network workstations under a public environment. It lets you restrict access to almost every corner of Windows for all PC workstations you have in your network, apply executable patches to them remotely, and schedule reboots, shutdowns, and Windows Explorer restarts from a single administrator's computer connected to a TCP/IP-based network or Internet. It is useful for any applications where you have to deal with lots of stand-alone PC workstations to be secured and constantly maintained. Once you install and configure the remote client service application on all your remote computers, you do not need to physically attend them anymore. In total, 1st Network Admin supports over 600 different security restrictions, options and tweaks.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
Best Mail Server is a fast SMTP/POP3 server program. Send mail from any client that is complaint with SMTP protocol, configure the server to be your local email server, or to accept email on behalf of your users and store it, until they retrieve it using POP3. The server delivers the easiest possible configuration, while lets you tweak any advanced features. Use the server along with any mailer or email program. Security features and options let you protect the server from DDoS attacks and safely block SPAM. SMTP and POP3 servers work as NT services therefore they will keep working in the logoff mode. Use multiple SMTP gateways in your server to deliver email in cases where direct delivery is not possible. Mailing lists functionality allows you to use this server as a mass mailer to send personalized messages. Try our Internet and email tools, free downloads.
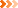 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
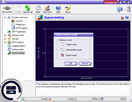
Corporate SMTP Server is a reliable high-performance SMTP server program for corporations and Internet Service Providers. It is simple and absolutely bullet-proof, it has a lot of security features and options you can use to protect the server from the outside of the Internet as well as safely block SPAM and spammers. It can be installed on several computers while the common message queue can be kept on a separate dedicated PC to increase sending power of your organization. This software works as a NT service therefore it will keep working in the logoff mode. For software debugging and testing purposes, the program has a testing mode. As a personal solution, it is ideal for laptop PC users who travel a lot and have to use different Internet Service Providers (ISP) on the run. The program lets you use SMTP gateway servers to achieve the best delivery rate where port 25 is blocked. Try our Internet and email tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
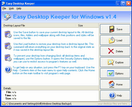
Backup, restore, manage and lock your desktop layout or layouts of PC users including placement of desktop icons, files and folders located on the desktop, desired wallpaper and screen saver. You can create desktop layouts for different purposes and provide users with their own desktops. Simply place your icons wherever you want them on your desktop, select desired wallpaper and screen saver, double click program's tray icon and click the Save button to create a new desktop layout file. If your icons ever get moved or deleted by any user or after entering the safe mode or changing the screen resolution, just open the program and click the Load button to return your desktop to any previously saved state, or simply reboot your PC if you are in the Lock Desktop mode. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |

Use this password-protected security utility to hide and lock your local, network, Floppy and USB drives as well as disable the AutoRun feature for them. The design of the program is very simple. The main window contains the boxes with drive settings that represent individual drives and the toolbar used for applying changes. All you need to do is to click on the checkboxes with settings and after you finish press the apply button. If desired, you can apply password protection to the program to prevent your users from changing the security settings you enforce. This software has a very nice easy-to-learn user interface. Excellent help system is also available. Try our security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
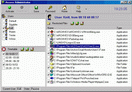
Backup and restore your Outlook Express data such as identities, email messages, email account settings, message rules, the address book, list of blocked senders, signatures and settings as well as backup and restore your Favorites, Windows Address Book and My Documents. The program produces encrypted archive files containing all your data, which you can put on a CD and use for transferring your data to a new PC. It has support for multiple user accounts and identities; you can move your data not only between identities of the same user, but also between different user accounts and computers. All users of your PC can maintain their own independent backups. Backups can be stored in a folder of your hard disk, put on CD, DVD or removable devices just by using standard Windows features. Try our Internet and email tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
When you use Windows, open folders, search for files and see pictures, work with different software, use the Internet and online banking to access your accounts, information about all your steps is stored in various files and in the registry. This fact results in security threat you may face because all pictures you have seen, all passwords and bank accounts you use and the other detailed activity information can be easily extracted and used against you by any person with a minimal computer knowledge. 1st Evidence Remover is a security system that lets you destroy all hidden needless activity information that may potentially contain evidence and endanger you needlessly. The program also removes temporary files left by your system making it cleaner and running faster. Try our password and security tools, free downloads.
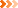 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
|
CD-DVD Lock - |
password protect CD/DVD/HDD/Floppy |
(v2.7) |
Password-protect and restrict read or write access to your drives such as CD, DVD, floppy, HDD with CD-DVD Lock. You can hide your devices from viewing or lock access to them. The program does not encrypt or alter your data in any way, therefore if you forget your password, you'll never lose your data stored on the protected media. The main purpose of the program is to restrict an ability of copying data between your drives as well as deny access to media itself. CD-DVD Lock will allow you avoid many of headaches connected with unauthorized software installations from any removable media and also prevent data leak by removable media. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
Password protect your files and folders, and restrict others from being able to start, see, change or delete them. File protection activates automatically according to the current user's identity and the timetable that is defined for it. You can keep your employees or kids off the Internet, games and the other entertainment during the working time. You can define a timetable and a list of restricted files for each user individually as you like. Also, Access Administrator may protect files from casual or unauthorized removal. The program is reliably protected by the password. Try our password and security tools, free downloads.
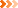 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
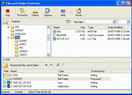
Protect your files and folders with File & Folder Protector at Windows kernel level. This great password-protected security utility lets you password-protect certain files and folders, or to hide them securely from viewing and searching just with a click of mouse. When PC user tries to access any protected file or folder, dialog box querying password appears on the screen. If entered password is valid, the user can access this file or folder, otherwise not. You can also use File & Folder Protector to protect your files and folders from casual or unauthorized removal. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
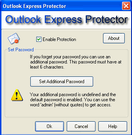
Outlook Express Protector is designed for controlling access to Outlook Express and its e-mail and address data bases. Outlook Express Protector does not encrypt protected files and folders, however no programs can get access to them when the program is active. When you try to start Outlook Express or open Address Book, Outlook Express Protector requests you to enter a password to grant access. If a user does not enter a valid password or cancels the authentication dialog box, Outlook Express or Address Book will not be opened and the data files will not be accessible for any third-party applications. This means that if Outlook Express Protector is active, nobody can steal or spoil your data you have in your Outlook Express. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
| |
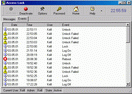
Access Lock is a system-tray security utility, which enables you to lock your PC with a password by two methods. The first one hides your desktop and shows a screen saver while the second one does not hide it allowing others to watch what happens there that is very useful when you would like to demonstrate something to people but do not want them to play with it. It also prevents unauthorized access on boot, logs the attemps of breaking the lock and allows people around to leave messages while the system is locked. Try our password and security tools, free downloads.
 More Info |
Screen Shots
|
Purchase | More Info |
Screen Shots
|
Purchase |
|
|
 |
 |
 |
|
|
|
|
|
|
|